Disk image formats¶
Disk Decipher supports these disk image formats:
If you use another disk image format and would like Disk Decipher to support that, please let me know.
VeraCrypt¶
From version 2.2.0, Disk Decipher supports VeraCrypt containers created by VeraCrypt 1.0 and later (header version 5). Almost all VeraCrypt features are supported:
- Operating mode: XTS
- Ciphers: AES-256, Serpent, Twofish, Kuznyechik, Camellia
- Cascade ciphers: AES-Twofish, AES-Twofish-Serpent, Serpent-AES, Serpent-Twofish-AES, Twofish-Serpent, Camellia-Kuznyechik, Camellia-Serpent, Kuznyechik-AES, Kuznyechik-Serpent-Camellia, Kuznyechik-Twofish
- Hash functions: SHA-512, SHA-256, Whirlpool, Streebog-512, BLAKE2s
- Deprecated hash function: RIPEMD160
- Argon2 key derivation
- Hidden volumes
- Keyfiles
- PIM (Personal Iterations Multiplier)
- Hidden Volume Protection
The PIM option is available under the advanced options, just tap on "Show advanced options" when mounting a disk to specify the PIM value.
Note that if you store your VeraCrypt images inside a folder which is synchronized to a cloud storage service like Dropbox or Box, you probably want to turn the VeraCrypt option "Preserve modification timestamp of file containers" off to allow the cloud storage agent to correctly detect changes to your VeraCrypt containers after unmount. Otherwise your VeraCrypt container will not be correctly synchronized to your cloud storage service.
Due to VeraCrypt's high number of hash algorithm iterations for key derivation, Disk Decipher will not try to detect the VeraCrypt disk image format for containers having a file extension registered to other disk formats (.tc, .vol and .dmg). To enable VeraCrypt disk image format detection, use VeraCrypt's default extension (.hc), an unrelated extension, or no extension at all, for your VeraCrypt container file.
Argon2
The official VeraCrypt distribution has not yet finalized the implementation details (currently in beta). Disk Decipher supports mounting an Argon2-protected container created with the VeraCrypt beta-version. During the VeraCrypt beta-period, Disk Decipher will not offer Argon2 when creating a new container.
RIPEMD-160 hash deprecated
Following the official VeraCrypt distribution, the RIPEMD-160 hash function has been deprecated. Unlike VeraCrypt, we have not removed this hash from Disk Decipher as it is difficult/impossible to download a previous app version from the App Store.
To mount a VeraCrypt container that uses the deprecated RIPEMD-160 hash function, expand the Advanced mount options and enable the "Deprecated algorithms" option.
It is recommended to migrate such containers by creating a new container, selecting all content of your current container and moving it to the new one.
Hidden Volume Protection¶
Version 6.2.1 introduces support for VeraCrypt's Hidden Volume Protection.
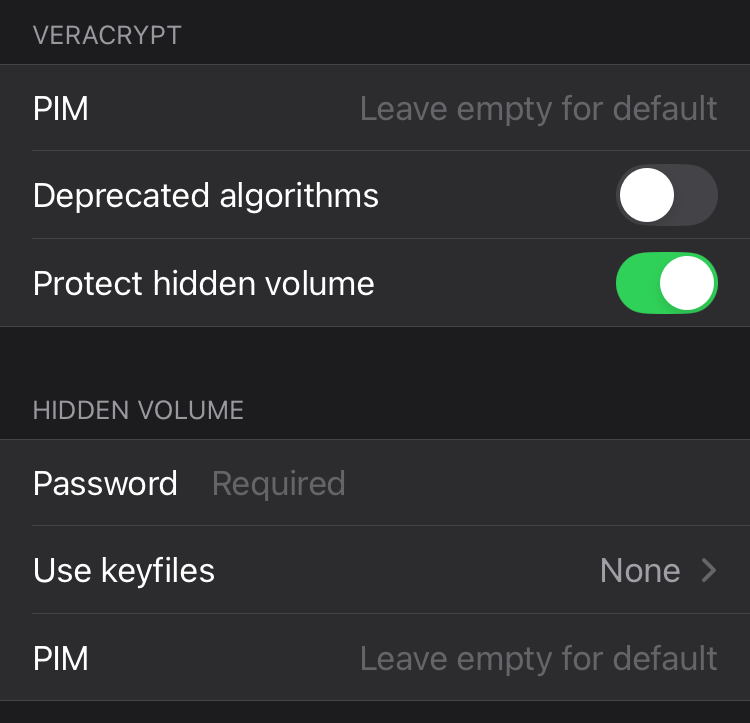
To enable this feature, unfold the advanced options in the mount dialog and select "Protect hidden volume" in the VeraCrypt section. This will reveal an additional "Hidden volume" section to specify the password of the hidden volume and, if applicable, any required keyfiles and custom PIM value.
Note
For obvious security reasons, none of the hidden volume protection related inputs will be saved, even if you enable the "Save password" option for the outer volume.
After a successful mount the hidden container protection will be active. In other words, if Disk Decipher is unable to protect the hidden volume, the mount operation will fail.
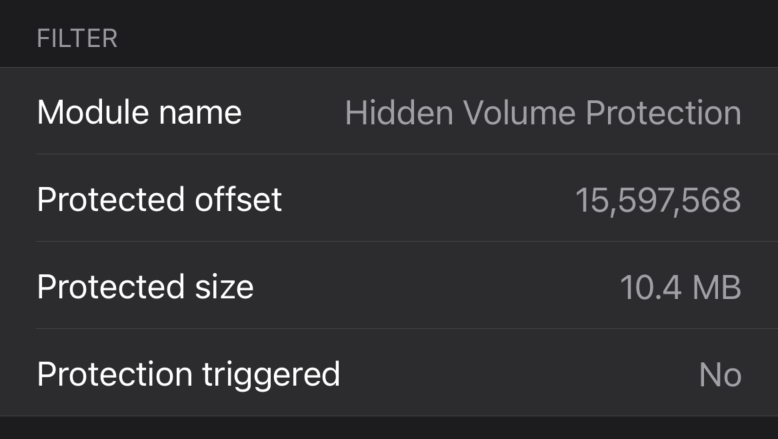
By tapping the (i) icon bottom right, you can verify that the protection is active: a module named "Hidden Volume Protection" should be present. The dialog also indicates if the protection has been triggered (forcing the mounted container to become read-only).
TrueCrypt¶
Disk Decipher supports TrueCrypt containers created by TrueCrypt 6.0 and later (header version 4 and 5). Almost all TrueCrypt features are supported:
- Operating mode: XTS
- Ciphers: AES-256, Serpent, Twofish
- Cascade ciphers: AES-Twofish, AES-Twofish-Serpent, Serpent-AES, Serpent-Twofish-AES, Twofish-Serpent
- Hash functions: RIPEMD160, SHA-512, Whirlpool
- Hidden volumes
- Keyfiles
Note that if you store your TrueCrypt images inside a folder which is synchronized to a cloud storage service like Dropbox or Box, you probably want to turn the TrueCrypt option "Preserve modification timestamp of file containers" off to allow the cloud storage agent to correctly detect changes to your TrueCrypt containers after unmount. Otherwise your TrueCrypt container will not be correctly synchronized to your cloud storage service.
LUKS¶
Disk Decipher supports LUKS volumes with version 1 and 2. The most common LUKS features are supported:
- Operating modes: XTS
- Ciphers: AES-256, Serpent, Twofish
- Hash functions: SHA1, SHA-256, SHA-512, RIPEMD160
- Sector size: 512, 1024, 2048 or 4096 bytes
- Keyfile
- Detached header (LUKS2)
To create a LUKS volume compatible with the above features, use commands like this on a Linux system:
# dd if=/dev/zero of=test.vol bs=1024 count=32768
# cryptsetup --type luks2 --cipher aes-xts-plain64 --key-size 512 --sector-size 512 luksFormat test.vol
# cryptsetup luksOpen test.vol test
# mke2fs -t ext4 /dev/mapper/test
# mount /dev/mapper/test /mnt
...
# umount /mnt
# cryptsetup luksClose test
Please note that LUKS2 uses the first 16 MB of the container as header, so you need to provide a container file larger than 16 MB. The example container above has size 32 MB resulting in approx. 15 MB free space inside the filesystem.
If you need support for other LUKS features (like CBC with ESSIV), please let me know.
Disk Decipher supports both PBKDF2 and Argon2 key derivation functions for LUKS2. Please note that Argon2 usually requires a large amount of memory (on purpose), which may prevent mounting your disk. For mobile devices, it is best to keep the memory parameter below 512 MB.
Detached header¶
LUKS2 supports an advanced setup called a "detached header". Instead of storing the LUKS2 header inside the disk image itself, the header is kept in a separate file. Disk Decipher now supports mounting LUKS2 containers that use such a detached header.
Why would you want this? Separating the header from the data adds a layer of security: you need both pieces to unlock the disk. It can also offer a basic form of plausible deniability—if someone only gets the data file, it doesn’t look like a usable LUKS2 container. In practice, this setup is useful when you want to keep the header stored elsewhere or alongside a keyfile.
In Disk Decipher, you can now select a detached header when mounting a LUKS2 disk. If you don’t choose one, Disk Decipher assumes the header is embedded in the container as usual. When you do choose one, Disk Decipher will use that file instead of reading the header from the disk image.
This feature is designed for compatibility with standard LUKS2 tools. As long as the detached header matches the container and was created with LUKS2 tooling, it should work across platforms.
How to use it¶
- Open the mount view for a LUKS2 disk.
- In the new “LUKS2” section, select “Detached header”.
- Choose the header file.
- Mount the disk as you normally would.
If you later want to remove the header selection, you can delete it from the same screen and the mount will revert to the embedded‑header workflow.
Important notes¶
A detached header is required only if the LUKS2 container was created that way. If you provide the wrong header, mounting will fail. Likewise, if the header file is missing or corrupted, the disk cannot be unlocked. Always keep a backup of the header file if you rely on this feature.
Creating a detached header¶
To create a LUKS2 container with a detached header, use commands like
dd if=/dev/zero of=data.img bs=1M count=10
dd if=/dev/zero of=header.img bs=1M count=4
cryptsetup luksFormat --type luks2 --header header.img data.img
cryptsetup open --header header.img data.img luksdev
mkfs.vfat /dev/mapper/luksdev
mount /dev/mapper/luksdev /mnt
...
umount /mnt
cryptsetup close luksdev
Apple Disk Image¶
Version 3.3.0 adds support for encrypted DMG files. The support covers
- Version 2 encrypted DMG (the default since OS X 10.5)
- Both AES-128 and AES-256 ciphers (all options offered by OS X)
- Password protected
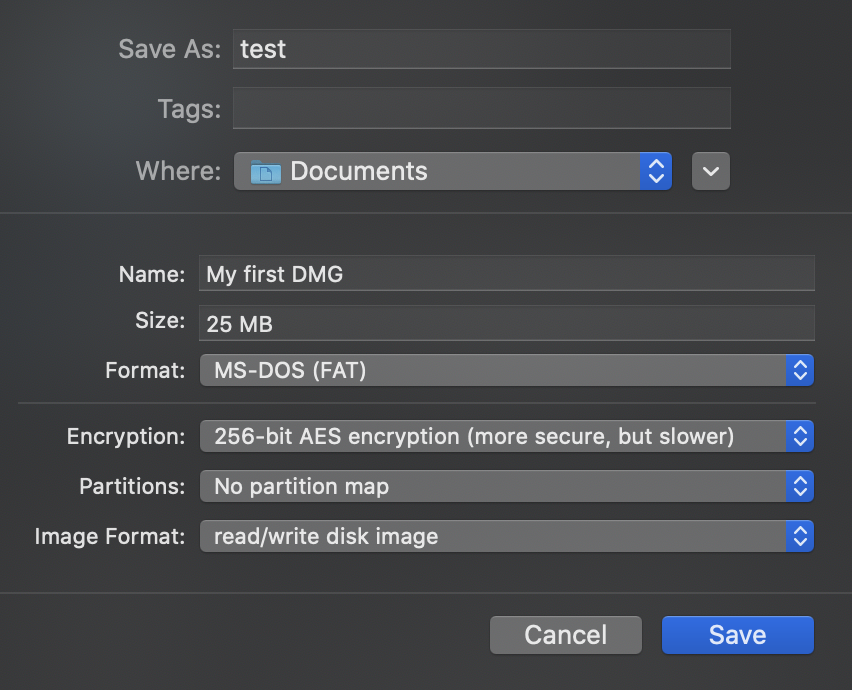
You can easily create a new container on macOS by using Disk Utility. Just select File -> New Image -> Blank Image and use settings like:
Do you prefer the commandline?
$ man hdiutil
$ hdiutil create -size 100m -layout NONE -fs FAT32 -encryption AES-256 -volname "MyLabel" test1.dmg
$ hdiutil create -size 25m -layout NONE -fs APFS -encryption AES-256 -volname "MyLabel" test2.dmg
$ hdiutil create -size 25m -layout NONE -fs ExFAT -encryption AES-256 -volname "MyLabel" test3.dmg
Finder will display the container with name "MyLabel" when mounting the container on macOS.
Compression¶
Versie 3.14.1 adds support for compressed DMG (i.e. both encrypted and compressed DMG).
These containers are readonly by design. The compression can greatly reduce the disk image size depending on the type of files stored inside the container.
The following compression algorithms are currently supported
- zlib
- LZFSE
- LZMA
To create a compressed DMG you can use Disk Utility on macOS (File - New Image - From Folder), or a command similar to these examples in Terminal
# zlib
$ hdiutil create -srcfolder ~/Documents/test -format UDZO -encryption AES-256 test_zlib.dmg
# LZFSE
$ hdiutil create -srcfolder ~/Documents/test -format ULFO -encryption AES-256 test_lzfse.dmg
# LZMA
$ hdiutil create -srcfolder ~/Documents/test -format ULMO -encryption AES-256 test_lzma.dmg
ProxyCrypt¶
Version 6.1.5 introduces support for the ProxyCrypt disk image format. ProxyCrypt is a niche format for advanced users.
Supported features:
- Volume format version 2
- Ciphers: AES-256, Serpent, SHACAL-2
- Cascaded ciphers
- Hash functions: Whirlpool, Keccak-512
- Custom scrypt parameters
- Keyfile
SHACAL-2
Disk images encrypted with SHACAL-2 are mounted readonly. Some encryption export/import declarations must be completed before
Disk Decipher is allowed to enable write support (encrypt data) for SHACAL-2.
If you need ProxyCrypt write support now, use AES-256 or Serpent (or a cascade of these ciphers).
Scrypt
If you use non-default Scrypt parameters, it is best to use 128 (default) or lower for the first parameter to prevent mount issues on mobile devices.
To create a new volume, use a command like
ProxyCrypt.exe X: -f test.vol -c 10M
ProxyCrypt.exe X: -f test.vol -c 10M -k keyfile
ProxyCrypt.exe X: -f test.vol -c 10M -sc 64,8
To unmount
and remount