Server Trust¶
Server Trust is an essential part of the security of HTTPS connections. Validation of the X.509 certificate presented by the server is critical to prevent man-in-the-middle and other attacks.
Even though the disk stored on the server is itself encrypted, establishing a secure connection is important for e.g. server authentication, data integrity and encrypting HTTP headers like Authorization containing the clear-text username and password when using basic authentication.
To establish server trust you have three options
- Public CA
- Private CA
- Certificate Trust
Public CA¶
In most cases, the best option is to provision the server with a certificate signed by a public Certificate Authority (CA). If the server you are connecting to is operated by a third party, this is their responsibility. Ask your service provider to fix any trust errors you encounter.
Validation of the server certificate is done by iOS / macOS for all HTTPS connections.
App Transport Security prevents connections without a valid server certificate.
If you operate the server (e.g. a NAS), check if your server supports Let's Encrypt or otherwise allows to request a certificate from an official CA.
Private CA¶
Instead of depending on a public CA, you can also operate your own private CA and provision certificates signed by your private CA.
This way, you can still satisfy the requirements of App Transport Security by adding your CA certificate to iOS / macOS.
Detailed instructions how to do this are available here.
Certificate Trust¶
Still, there are valid use cases where it is perfectly fine to use a certificate that iOS / macOS does not trust by default, e.g. when your NAS is located on your LAN and provisioned with a self-signed certificate.
Disk Decipher 3.9 allows you to trust a certificate for a remote disk, thus allowing the app to connect to the server. It is your responsibility to check that the certificate is indeed the one used by your server, and the trust errors displayed do not impact your security.
When you connect to a HTTPS server with an untrusted certificate, an alert will be displayed with the exact trust errors, like
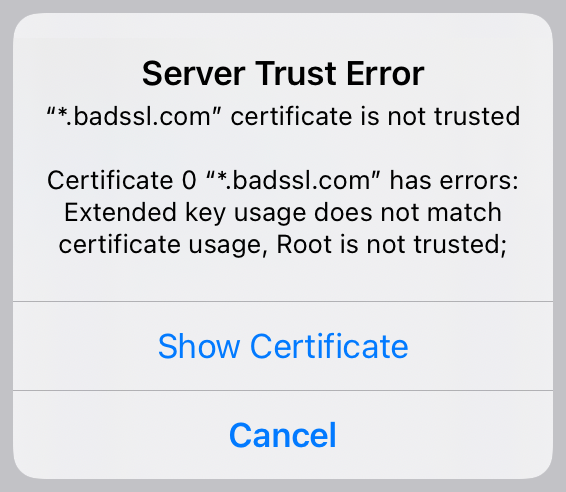
If you select Show Certificate more information is shown about the certificate presented by the server
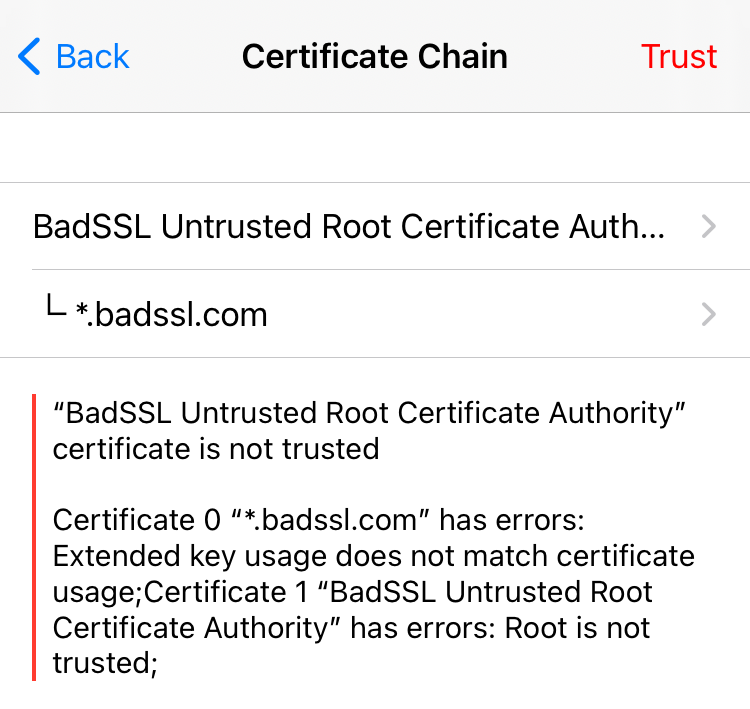
You can tap on any certificate in the chain to obtain more detailed information of that certificate, including the fingerprints.
If you are confident that the certificate is trustworthy for your use case, tap the Trust button to trust the certificate.
The Trust button is currently only available in the Disk Decipher app, not when mounting a disk using the iOS File Provider. Any trust added inside the Disk Decipher app will be used by the iOS File provider too.
The trusted certificate will be bound to the remote disk. You can review this in the Disk Settings.