Keyfiles¶
Version 1.9 adds TrueCrypt and VeraCrypt keyfile support to Disk Decipher. If you need keyfile support for other disk formats (e.g. LUKS) let me know.
Version 3.20 changes the way Disk Decipher interacts with keyfiles. To improve the security of the keyfiles, keyfiles remain stored outside of the app (instead of importing keyfiles into the iOS keychain) and are selected/read when mounting a disk, similar to the way desktop applications use keyfiles. This allows you to store keyfiles separate from the device on which you use Disk Decipher. Of course, if you prefer, the keyfiles can be stored on the same device.
Version 5.4 adds support for reading keyfiles from a smart card. More details in the Smart Cards section below.
Using keyfiles¶
To use keyfiles when mounting a disk, simply tap the "Select keyfiles..." option
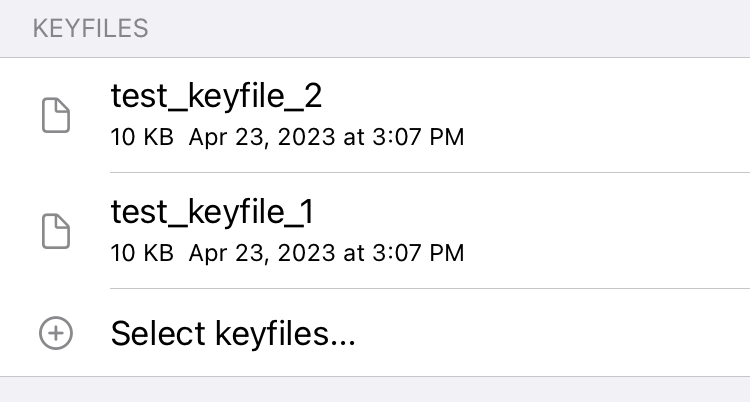
This allows you to select the keyfiles you want to use. You can select multiple files at once and also use this option multiple times.
To delete a file that was selected by mistake, swipe the entry from right to left as usual.
Deleting a keyfile¶
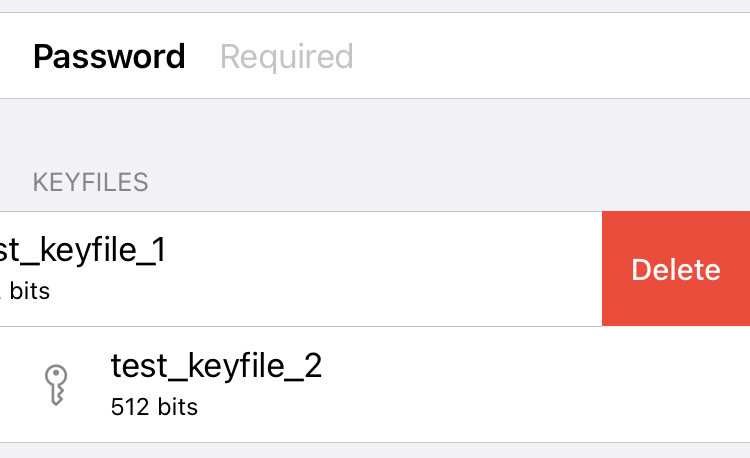
If you have a pre-version 3.20 keyfile imported in Disk Decipher, it is best to delete it from the app. Of course, only delete it from the app if you have the original keyfile available!
If you want to delete a keyfile from Disk Decipher, simply swipe from right to left on the keyfile you want to delete, and tap the Delete button that is presented. The keyfile will be deleted from the iOS keychain.
Smart Cards¶
Version 5.4 adds initial support for reading keyfiles from a smart card. On the mount (or create) dialog just select "Read smart card" in the Keyfiles section.
The implementation is designed to be compatible with VeraCrypt to allow cross-platform access to smart card protected containers.
This feature has been tested successfully with these smart cards:
- YubiKey 5C NFC (connected using USB-C)
- YubiKey NEO (connected using USB-A)
Compatibility with other smart cards is important, so please let me know if you successfully use another smart card brand or type so I can update this list.
If your smart card is not working, please open an issue so we can investigate this.
The current implementation has this limitation:
- Disk Decipher currently reads the Fingerprints object (0x5FC103) from the smart card. This is hardcoded. This will be extended in one of the next updates, so you can select other data objects too. If you have an interest in a specific object, please let me know.
Note
When connecting a YubiKey to an iOS device without external keyboard, the on-screen keyboard might not appear when you need to enter the PIN, due to the YubiKey emulating a keyboard.
To mitigate this, Disk Decipher presents an additional bar containing the numeric keys enabling you to enter your PIN.
If your PIN code contains non-numeric characters (which is not recommended), you can workaround this by disabling the OTP application on the YubiKey (only for the interface used to connect to your device) using the YubiKey Manager. Changing the PIN code is a more pragmatic workaround.
To initialize the Fingerprints object (0x5FC103) of a YubiKey, you have two options:
- Use the commandline YubiKey manager:
- Use the VeraCrypt app on Mac or Windows desktop to create a new smartcard-based keyfile, make sure to select the Fingerprints object when prompted