Disk image formats¶
Disk Decipher supports these disk image formats:
- TrueCrypt (https://en.wikipedia.org/wiki/TrueCrypt)
- FreeOTFE (https://en.wikipedia.org/wiki/FreeOTFE)
- LUKS (https://gitlab.com/cryptsetup/cryptsetup/)
- VeraCrypt (https://www.veracrypt.fr/)
- Apple Disk Image (encrypted DMG)
If you use another disk image format and would like Disk Decipher to support that, please let me know.
TrueCrypt¶
Disk Decipher supports TrueCrypt containers created by TrueCrypt 6.0 and later (header version 4 and 5). Almost all TrueCrypt features are supported:
- Operating mode: XTS
- Ciphers: AES-256, Serpent, Twofish
- Cascade ciphers: AES-Twofish, AES-Twofish-Serpent, Serpent-AES, Serpent-Twofish-AES, Twofish-Serpent
- Hash functions: RIPEMD160, SHA-512, Whirlpool
- Hidden volumes
- Keyfiles
Note that if you store your TrueCrypt images inside a folder which is synchronized to a cloud storage service like Dropbox or Box, you probably want to turn the TrueCrypt option "Preserve modification timestamp of file containers" off to allow the cloud storage agent to correctly detect changes to your TrueCrypt containers after unmount. Otherwise your TrueCrypt container will not be correctly synchronized to your cloud storage service.
FreeOTFE¶
Disk Decipher supports FreeOTFE volumes with version 3 and 4. The most common FreeOTFE features are supported:
- Operating modes: XTS, CBC
- Ciphers: AES-256, Serpent, Twofish, Blowfish-448
- Hash functions: RIPEMD160, SHA-512, Whirlpool
- Custom key iterations and salt length
Other advanced FreeOTFE features are currently not supported, like keyfiles and hidden volumes. If you would like support for such a feature added to Disk Decipher, please let me know.
LUKS¶
Disk Decipher supports LUKS volumes with version 1 and 2. The most common LUKS features are supported:
- Operating modes: XTS
- Ciphers: AES-256, Serpent, Twofish
- Hash functions: SHA1, SHA-256, SHA-512, RIPEMD160
- Sector size: 512, 1024, 2048 or 4096 bytes
- Keyfile
To create a LUKS volume compatible with the above features, use commands like this on a Linux system:
# dd if=/dev/zero of=test.vol bs=1024 count=32768
# cryptsetup --type luks2 --cipher aes-xts-plain64 --key-size 512 --sector-size 512 luksFormat test.vol
# cryptsetup luksOpen test.vol test
# mke2fs -t ext4 /dev/mapper/test
# mount /dev/mapper/test /mnt
...
# umount /mnt
# cryptsetup luksClose test
Please note that LUKS2 uses the first 16 MB of the container as header, so you need to provide a container file larger than 16 MB. The example container above has size 32 MB resulting in approx. 15 MB free space inside the filesystem.
If you need support for other LUKS features (like CBC with ESSIV), please let me know.
Disk Decipher supports both PBKDF2 and Argon2 key derivation functions for LUKS2. Please note that Argon2 usually requires a large amount of memory (on purpose), which may prevent mounting your disk inside the iOS File Provider, since iOS limits the iOS File Provider to 15 MB of RAM.
VeraCrypt¶
From version 2.2.0, Disk Decipher supports VeraCrypt containers created by VeraCrypt 1.0 and later (header version 5). Almost all VeraCrypt features are supported:
- Operating mode: XTS
- Ciphers: AES-256, Serpent, Twofish, Kuznyechik, Camellia
- Cascade ciphers: AES-Twofish, AES-Twofish-Serpent, Serpent-AES, Serpent-Twofish-AES, Twofish-Serpent, Camellia-Kuznyechik, Camellia-Serpent, Kuznyechik-AES, Kuznyechik-Serpent-Camellia, Kuznyechik-Twofish
- Hash functions: RIPEMD160, SHA-512, SHA-256, Whirlpool, Streebog-512, BLAKE2s
- Hidden volumes
- Keyfiles
- PIM (Personal Iterations Multiplier)
The PIM option is available under the advanced options, just tap on "Show advanced options" when mounting a disk to specify the PIM value.
Note that if you store your VeraCrypt images inside a folder which is synchronized to a cloud storage service like Dropbox or Box, you probably want to turn the VeraCrypt option "Preserve modification timestamp of file containers" off to allow the cloud storage agent to correctly detect changes to your VeraCrypt containers after unmount. Otherwise your VeraCrypt container will not be correctly synchronized to your cloud storage service.
Due to VeraCrypt's high number of hash algorithm iterations for key derivation, Disk Decipher will not try to detect the VeraCrypt disk image format for containers having a file extension registered to other disk formats (.tc, .vol and .dmg). To enable VeraCrypt disk image format detection, use VeraCrypt's default extension (.hc), an unrelated extension, or no extension at all, for your VeraCrypt container file.
Apple Disk Image¶
Version 3.3.0 adds support for encrypted DMG files. The support covers
- Version 2 encrypted DMG (the default since OS X 10.5)
- Both AES-128 and AES-256 ciphers (all options offered by OS X)
- Password protected
You can easily create a new container on macOS by using Disk Utility. Just select File -> New Image -> Blank Image and use settings like:
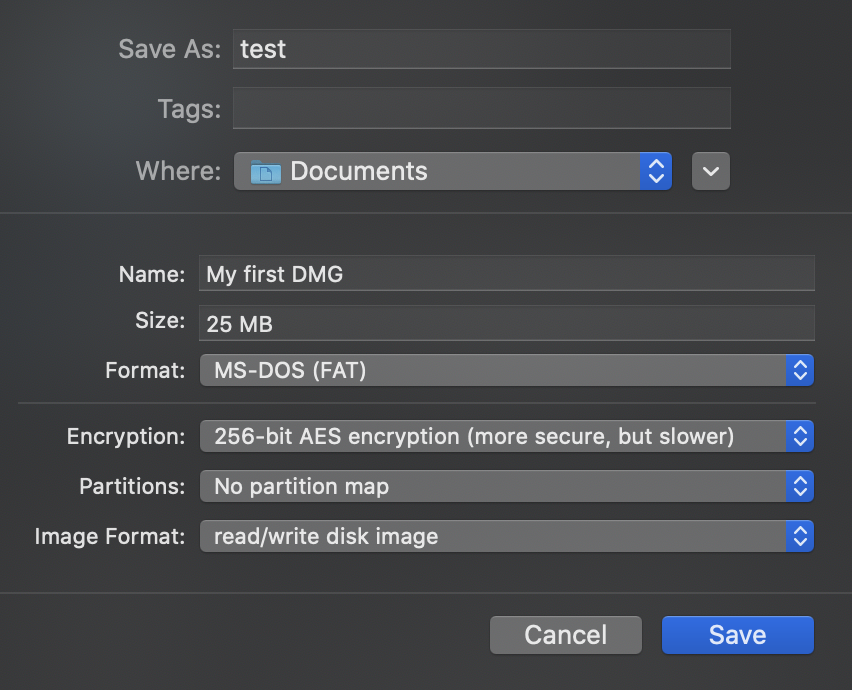
Do you prefer the commandline?
$ man hdiutil
$ hdiutil create -size 100m -layout NONE -fs FAT32 -encryption AES-256 -volname "MyLabel" test1.dmg
$ hdiutil create -size 25m -layout NONE -fs APFS -encryption AES-256 -volname "MyLabel" test2.dmg
$ hdiutil create -size 25m -layout NONE -fs ExFAT -encryption AES-256 -volname "MyLabel" test3.dmg
Finder will display the container with name "MyLabel" when mounting the container on macOS.
Compression¶
Versie 3.14.1 adds support for compressed DMG (i.e. both encrypted and compressed DMG).
These containers are readonly by design. The compression can greatly reduce the disk image size depending on the type of files stored inside the container.
The following compression algorithms are currently supported
- zlib
- LZFSE
- LZMA
To create a compressed DMG you can use Disk Utility on macOS (File - New Image - From Folder), or a command similar to these examples in Terminal
# zlib
$ hdiutil create -srcfolder ~/Documents/test -format UDZO -encryption AES-256 test_zlib.dmg
# LZFSE
$ hdiutil create -srcfolder ~/Documents/test -format ULFO -encryption AES-256 test_lzfse.dmg
# LZMA
$ hdiutil create -srcfolder ~/Documents/test -format ULMO -encryption AES-256 test_lzma.dmg